How to Secure Magento 2: The Ultimate 9-Step Guide






Securing your e-commerce Magento 2 website is crucial for the protection of your online store and the sensitive data of your customers. Implementing security features and extensions, as well as conducting regular security audits, are essential for maintaining a secure online environment. With the increasing number of cyber threats targeting e-commerce platforms, it is essential to implement robust security measures to safeguard your Magento website's security. This is especially important for default Magento installations, as they are more vulnerable to malware attacks. Additionally, regular backups of your Magento website are crucial to protect your data and ensure quick recovery in case of any security breaches.
Magento 2, being a popular e-commerce platform, is not immune to potential security risks that websites and store owners should be aware of. It is important for users to have a strong password in order to protect their online stores from possible hacks. From unauthorized access to data breaches and malware attacks, there are various vulnerabilities that can compromise the security of your Magento website. Protect your e-commerce store with robust security features to prevent Magento security issues.
By implementing stringent security measures for your e-commerce store, you can ensure the safety of your customer's personal information and maintain trust in your brand. Store owners should regularly update their passwords and create a backup to prevent financial losses due to fraudulent activities.
Understanding Magento 2 Security Standards
To ensure the security of your e-commerce store, it is crucial to familiarize yourself with Magento's security guidelines. This includes setting a strong password for your admin account, regularly backing up your website data, and managing your store's cookies effectively. These guidelines outline the best practices and standards that should be followed to protect your e-commerce store from potential threats and vulnerabilities. It is crucial to prioritize Magento security by implementing security extensions and conducting regular security audits.
Familiarizing yourself with Magento's security guidelines
Magento provides comprehensive documentation on security practices for your e-commerce store that you should consider implementing to back up and protect your site hosted on the platform. By understanding these guidelines for Magento security, you can take proactive measures to safeguard your store and customer data. This includes conducting a security audit and utilizing security extensions to enhance store security. Some key areas covered in Magento's security guidelines include:
- Assigning appropriate user roles and permissions on your site is key to controlling access during a session. This helps control access to sensitive information within your store. Limiting access to the store security site only to those who require it reduces the risk of unauthorized activities in an e-commerce store, such as a Magento store.
- Complying with industry best practices for secure coding is essential in building a robust and secure Magento 2 e-commerce store. This includes using strong encryption algorithms to secure your site, validating user input on your e-commerce store, and keeping software components up-to-date on your Magento store.
- Implementing strong password policies is crucial for protecting administrator accounts and preventing unauthorized access to your site, especially for your Magento store. Encourage users of your Magento store site to create unique, complex passwords and regularly update them.
- Configuring proper file system permissions on your site ensures that only authorized users can modify critical files or directories on your server. Restricting write access to sensitive files on a site helps prevent malicious activities.
Complying with industry best practices for secure coding
Following industry best practices for secure coding is vital for protecting your Magento 2 website against common vulnerabilities such as cross-site scripting (XSS) or SQL injection attacks. Here are some tips to enhance the security of your code on your site.
- Site input validation is crucial in order to prevent malicious code injection into your application. Validate all user input thoroughly before processing it.
- Properly escape output data on web pages to prevent XSS attacks on your site.
- Secure configuration settings: Ensure that your Magento installation uses secure configuration settings, such as enabling two-factor authentication (2FA) for admin accounts and using secure HTTPS connections.
Understanding the importance of regular security audits
Regular security audits are crucial for identifying any vulnerabilities or weaknesses in your Magento 2 website. These audits help you stay one step ahead of potential threats and ensure that your online store remains secure. Here's why regular security audits are important:
- Identifying vulnerabilities: Security audits can uncover any existing vulnerabilities in your website's code, configurations, or infrastructure. This allows you to address them promptly before they can be exploited by malicious actors.
- Staying compliant: Regular security audits help ensure that your website complies with industry standards and regulations, such as the Payment Card Industry Data Security Standard (PCI DSS). Compliance is essential for maintaining trust with customers and avoiding penalties.
- Protecting customer data: By conducting security audits, you demonstrate a commitment to protecting customer data. This helps build trust among your customers and enhances the reputation of your online store.
Implementing Two-Factor Authentication
Enhancing login security is crucial in protecting your Magento 2 store from unauthorized access. One effective way to achieve this is by implementing two-factor authentication (2FA). This additional layer of security requires users to provide two forms of identification before gaining access to their accounts.
Enhancing login security with two-factor authentication
By enabling two-factor authentication, you add an extra step to the login process, making it more challenging for hackers to gain unauthorized access. It acts as a safeguard against brute force attacks and password breaches. Even if hackers manage to obtain a user's password, they would still need the second factor (such as a unique code) to successfully log in.
To enable 2FA for your Magento 2 store, follow these steps:
- Install a reliable two-factor authentication extension from the Magento Marketplace.
- Configure the extension settings according to your preferences.
- Choose the desired 2FA method, such as SMS verification or authenticator apps like Google Authenticator or Authy.
- Customize the settings for each method, such as setting up trusted devices or IP whitelisting.
Configuring trusted devices for a smoother user experience
While implementing 2FA adds an extra layer of security, it can sometimes inconvenience users by requiring them to provide additional information during every login attempt. To address this issue and ensure a smoother user experience, you can configure trusted devices.
With trusted devices enabled, users can mark their personal devices (such as smartphones or laptops) as "trusted" after successfully completing the 2FA process once. Subsequent logins from these trusted devices will not require another round of two-factor authentication unless specific conditions are met (e.g., suspicious activity is detected).
Configuring trusted devices helps strike a balance between security and convenience for both users and administrators.
Utilizing popular two-factor authentication methods like SMS or authenticator apps
There are several popular methods available for implementing two-factor authentication in Magento 2:
- SMS Verification: Users receive a unique code via SMS to their registered mobile number, which they need to enter during the login process.
- Authenticator Apps: Users can install authenticator apps like Google Authenticator or Authy on their smartphones. These apps generate time-based one-time passwords (TOTPs) that users must enter along with their passwords.
Both methods provide an additional layer of security by requiring users to possess something they know (their password) and something they have (the unique code from SMS or authenticator app).
By utilizing these popular two-factor authentication methods, you strengthen the security measures of your Magento 2 store and protect sensitive information from unauthorized access.
Implementing two-factor authentication is a crucial step toward securing your Magento 2 store from potential threats. It adds an extra layer of protection against hackers attempting to force their way into your application. By following the steps outlined above and utilizing trusted devices and popular authentication methods, you can significantly enhance the login security for your Magento 2 store.
Configuring Admin User Accounts and Permissions
To secure your Magento 2 store, it's crucial to configure admin user accounts and permissions effectively. By creating unique admin accounts for each user with specific roles and permissions, you can limit access to sensitive areas based on job responsibilities. Regularly reviewing and updating admin account privileges is also essential to maintain a secure environment.
Creating Unique Admin Accounts
When setting up your Magento 2 store, it's important to create individual admin accounts for each user who will have access to the admin panel. This ensures accountability and allows you to track actions performed by different users. Each admin account should have a unique username and password combination, making it harder for unauthorized individuals to gain access.
By assigning specific roles and permissions to each admin user, you can control what they can do within the system. For example, you may have one admin user responsible for managing products while another focuses on order fulfillment. This segregation of duties helps prevent unauthorized changes or malicious activity.
Limiting Access Based on Job Responsibilities
To further enhance security, limit access to sensitive areas of your Magento 2 store based on job responsibilities. Not every administrator needs full access to all system settings or customer data. By granting only the necessary permissions required for their role, you reduce the risk of accidental or intentional misuse of privileges.
Magento 2 provides a comprehensive list of predefined roles that you can assign to different admin users. These roles define which sections of the administration panel are accessible and what actions can be performed within those sections. You can also create custom roles if needed, tailoring them specifically to your business requirements.
Regularly Reviewing and Updating Admin Account Privileges
As part of ongoing security measures, it's crucial to regularly review and update admin account privileges in Magento 2. This involves periodically assessing whether an administrator still requires certain permissions or if any adjustments need to be made based on changes in job responsibilities.
By regularly reviewing admin account privileges, you can ensure that access is granted only where necessary. This helps minimize the potential for unauthorized changes or data breaches. Removing unnecessary permissions reduces the attack surface and strengthens the overall security posture of your Magento 2 store.
Securing Admin Access and URLs
To ensure the security of your Magento 2 website, it is crucial to take steps to secure admin access and URLs. By implementing these measures, you can protect your admin panel from unauthorized access attempts and potential security risks.
Renaming Default Admin URL
One effective way to enhance the security of your Magento 2 website is by renaming the default admin URL. By default, the admin URL is set to "/admin" or "/backend," which makes it an easy target for hackers. Renaming the admin URL adds an extra layer of protection by making it harder for unauthorized individuals to find the login page.
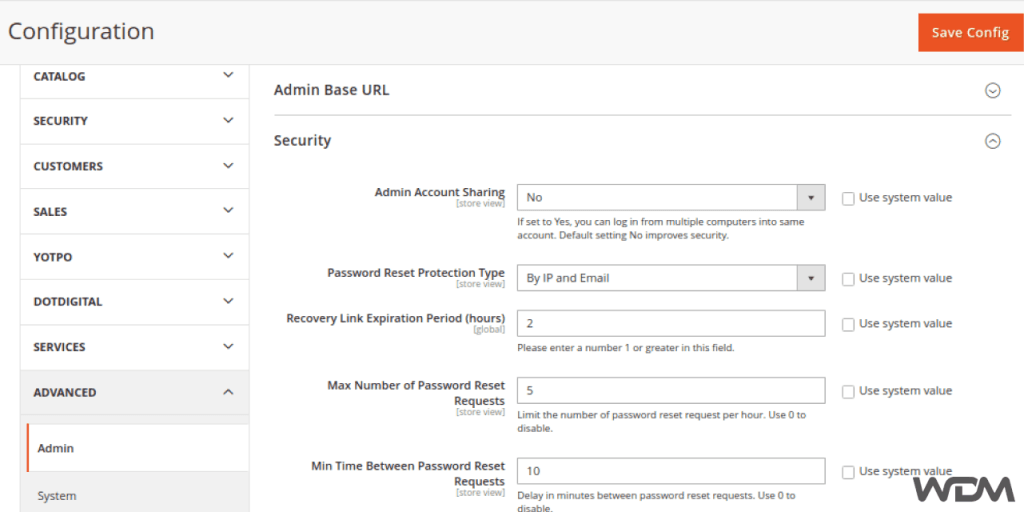
Enforcing Strong Passwords for Admin Accounts
Another essential step in securing your Magento 2 website is enforcing strong passwords for all admin accounts. Weak passwords are vulnerable to brute force attacks, where hackers systematically try different combinations until they find a match. By requiring complex passwords with a mix of uppercase and lowercase letters, numbers, and special characters, you significantly reduce the risk of unauthorized access.
Restricting IP Addresses that Can Access the Admin Panel
Limiting access to the admin panel based on IP addresses adds an additional level of security. By configuring your server or using security extensions, you can specify which IP addresses are allowed to access the admin area. This restricts access only to trusted networks or specific locations, making it more difficult for potential attackers to gain entry.
Implementing these measures helps safeguard your Magento 2 website from various security threats and potential breaches. However, it's important not to rely solely on these methods; other security practices should be employed as well.
Here are some pros and cons related to securing admin access and URLs:
Pros:
- Renaming the default admin URL makes it harder for hackers to find the login page.
- Enforcing strong passwords reduces vulnerability against brute-force attacks.
- Restricting IP addresses limits access only to trusted networks or specific locations.
Cons:
- Renaming the admin URL may require additional configuration and maintenance.
- Enforcing strong passwords might lead to users forgetting their passwords more frequently.
- Restricting IP addresses can be challenging if your team members need to access the admin panel remotely.
Keeping Magento Up to Date with Patches
To ensure the security of your Magento 2 website, it is crucial to keep it up to date with the latest patches. Installing security patches promptly helps protect your online store from vulnerabilities and potential hacks. Here are some key points to consider when it comes to keeping Magento up to date with patches:
Importance of installing security patches promptly
Installing security patches as soon as they become available is essential for maintaining a secure Magento website. These patches often address known vulnerabilities and weaknesses that could be exploited by hackers. By promptly applying these updates, you can stay one step ahead and minimize the risk of potential security breaches.
Regularly checking for available updates from Magento
Magento regularly releases updates and security patches to address any identified issues or vulnerabilities in their software. It is crucial for store owners or developers to regularly check for these updates and apply them promptly. By staying informed about the latest releases, you can ensure that your website remains secure and protected.
Utilizing automated tools to streamline the patch management process
Managing and applying patches manually can be time-consuming and prone to human error. To streamline the patch management process, consider utilizing automated tools specifically designed for Magento websites. These tools can help automate the detection, download, and installation of necessary updates, saving you valuable time while ensuring that your website remains secure.
Using automated tools has several benefits:
- Saves time: Automated tools can significantly reduce the time required for manual patch management tasks.
- Minimizes errors: Human errors during manual patch installations can lead to issues or potential vulnerabilities in your website's code.
- Streamlines workflow: Automated tools provide a streamlined workflow by automating repetitive tasks associated with patch management.
By leveraging these tools, you can simplify the process of keeping your Magento store up to date with the latest security patches.
Monitoring and Auditing Custom Modules
To ensure the security of your Magento 2 store, it's crucial to regularly monitor and audit the custom modules you have installed. This involves conducting code reviews and vulnerability assessments on these modules, as well as keeping a close eye on their activity logs for any suspicious behavior.
Regular Code Reviews and Vulnerability Assessments
Performing regular code reviews on your custom modules is essential for identifying any potential security vulnerabilities. This involves examining the codebase to check for any insecure coding practices or loopholes that could be exploited by attackers. By conducting these reviews, you can proactively address any weaknesses in your custom modules before they are exploited.
In addition to code reviews, vulnerability assessments should also be carried out periodically. These assessments involve using specialized tools to scan your custom modules for known vulnerabilities or weaknesses. By identifying these vulnerabilities early on, you can take appropriate measures to patch or mitigate them effectively.
Ensuring Third-Party Extensions Are from Reputable Sources
When installing third-party extensions for your Magento 2 store, it's crucial to ensure that they come from reputable sources. Using extensions from unknown or untrusted sources increases the risk of introducing security vulnerabilities into your store. Therefore, always obtain extensions from trusted marketplaces or directly from reputable developers.
Before installing a third-party extension, conduct some research on the developer or marketplace providing it. Look for user reviews and ratings to gauge the reliability and security track record of the extension provider. Check if they provide regular updates and support for their products.
Monitoring Module Activity Logs
Monitoring module activity logs are an important part of securing Magento 2 stores with custom modules. These logs provide valuable insights into how the modules are functioning and whether there are any suspicious activities occurring within them.
By regularly reviewing module activity logs, you can detect any unusual behavior such as unauthorized access attempts or unexpected changes in configuration settings. If you notice anything suspicious, take immediate action to investigate and address the issue. This could involve disabling or removing the affected module, as well as implementing additional security measures to prevent further unauthorized access.
Best Practices for Magento Security
By understanding Magento security standards, implementing two-factor authentication, configuring admin user accounts and permissions, securing admin access and URLs, keeping Magento up to date with patches, and monitoring custom modules, you are taking crucial steps towards safeguarding your online business.
Now that you have a solid foundation in Magento security best practices, it's time to put them into action. Take the necessary steps to implement these measures on your website and regularly review and update your security protocols. Remember, securing your Magento store is an ongoing process that requires vigilance and proactive measures.
Frequently Asked Questions
What are some common security vulnerabilities in Magento?
Security vulnerabilities in Magento can include weak passwords, outdated software versions, insecure extensions or themes, improper file permissions, SQL injections, cross-site scripting (XSS), and brute force attacks. It's essential to address these vulnerabilities by following best practices for password management, keeping software up to date with patches and updates, using trusted extensions/themes from reputable sources only after thorough vetting, setting proper file permissions to restrict unauthorized access, and implementing security measures like firewalls and intrusion detection systems.
How often should I update my Magento store with patches?
It is recommended to stay up to date with the latest patches released by Magento. Regularly check for new patch releases and apply them promptly after testing them in a development environment. Patches often address critical security vulnerabilities or bugs that could be exploited by malicious actors. By keeping your store updated with patches, you ensure that potential vulnerabilities are addressed promptly.
Is two-factor authentication necessary for my Magento store?
Two-factor authentication adds an extra layer of security by requiring users to provide two forms of identification before accessing their accounts. It is highly recommended to enable two-factor authentication for all admin user accounts in your Magento store. This additional step helps protect against unauthorized access, even if passwords are compromised. Implementing two-factor authentication is a simple yet effective way to enhance the security of your Magento store.
How can I monitor and audit custom modules in Magento?
Monitoring and auditing custom modules is crucial to ensure their security and stability. Regularly review the code of custom modules for any potential vulnerabilities or insecure practices. Utilize tools like static code analyzers or security scanners to identify any weaknesses in your codebase. Keep track of updates or patches released by module developers and promptly apply them to address any known security issues.
What should I do if my Magento store gets hacked?
If your Magento store gets hacked, it's important to act quickly to minimize damage and restore security. Take the following steps:
- Immediately take your site offline to prevent further unauthorized access.
- Identify the source of the breach by analyzing logs and investigating suspicious activity.
- Restore your website from a clean backup taken before the compromise occurred.
- Change all passwords associated with your Magento admin accounts, hosting provider, FTP/SFTP access, etc.
- Conduct a thorough security audit to identify any vulnerabilities that may have been exploited.
- Implement additional security measures such as firewalls, web application firewalls (WAF), and intrusion detection systems (IDS) to prevent future attacks.
Remember, prevention is key. By implementing proper security measures and staying vigilant, you can protect your online business from potential threats and ensure a safe shopping experience for your customers.

